Mitigate threats across the entire attack surface faster, more reliably than SIEM
GET A DEMOHunters SOC Platform offloads the critical burden of data engineering and manual analyst workflows, enabling teams to automatically identify and respond to threats with ease and scale.
UNLIMITED
INGEST AT
1/4 COST
INGEST WITH EASE
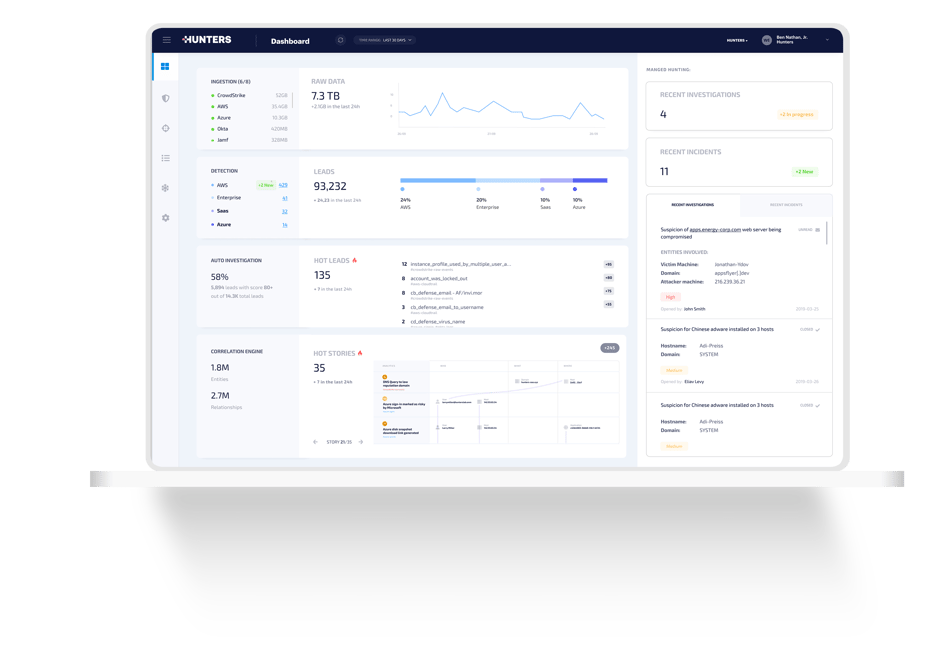
Seamlessly Ingest and Organize all Your Data
Enable security teams to leverage all data sources across domains (cloud, endpoint, network, identity, email, etc.) without compromise.
Unlimited data is seamlessly ingested and mapped into a unified schema, ready for the detection and investigation workflow.
- Automatically ingest unlimited amounts of data from all data sources
- Organize data across domains into a unified schema without data engineering efforts
- Maintain data in "always-hot" storage at a predictable cost
88%
REDUCTION
IN MTTD
DETECT ACROSS THE ATTACK SURFACE
Leverage a Built-in Detection Engine for Scale and Accuracy
Remove the burden of ongoing rules creation and maintenance with an always up-to-date detection engine that surfaces and enriches disparate signals across data sources.
- Gain out-of-the-box attack surface coverage
- Go beyond UEBA to spot user-based attacks as well as attacks compromising other entities
- View your threat coverage and identify gaps based on the MITRE ATT&CK framework
85% REDUCTION
IN INVESTIGATION
TIME
UNDERSTAND "WHO, WHAT, WHERE, WHEN"
Realize the Power of Auto Investigation
Stop chasing false positives and remove exhaustive, repetitive work to focus the analyst efforts on triage and response.
Unique graph-based correlation automatically links relevant data, simplifying triage and accelerating time to understand the attack.
- Focus on a list of prioritized incidents based on their risk score
- See the entire attack story with its details, including root cause, timeline, affected users, endpoints and related entities and more
- Cut attackers' dwell time with clear context and remediation steps
BETTER SECURITY OUTCOMES
THE HUNTERS
DIFFERENCE
Fastest Time-To-Value
Get results quickly with seamless data ingest and built-in detection
Reduce Overhead
Eliminate manual data engineering and detection rules maintenance
Unlimited Scale
Ingest and organize unlimited amounts of data, at a predictable cost
Streamlined Investigation
Minimize false-positives and focus on real incidents
OUR CUSTOMERS