As soon as a threat or vulnerability (such as Log4Shell) is discovered or announced, Team Axon researches the threat and investigates your environment for potential impact and risk by utilizing relevant IOCs and TTPs.
TEAM
Your resident threat hunters
Their mission: Help your security team protect your organization, through prompt and reliable cyber expertise.
See them in actionRAPID RESPONSE
New threat? Researched it.
How it works:
1.
2.
The team issues an advisory and practical hunting tools to all customers, via email, Twitter, GitHub, blog posts, and the Rapid Response status page.
Advisories include:
- Information about the threat
- Mitigation recommendations
- Hunting queries
- Additional resources
3.
If there’s suspicion that you’ve been affected, Team Axon reaches out individually with a full report detailing what happened and next steps.
4.
Relevant detection methods are implemented in the platform, providing immediate coverage against imminent threats and extending future automation to all Hunters customers.
EXPERT INVESTIGATION ASSISTANCE
Who you gonna call?
Whether you need a hand with a particular investigation, or just a second opinion, someone from Team Axon will be there to provide advice and assistance.
Consult an Axon Expert
General assistance and consultation with the Axon team.
This can include topics such as:
- Investigating particular signals or alerts in the product
- Developing hunting queries
- Guidance on new and emerging threats or vulnerabilities
Axon Incident Investigation
If you need help dealing with an incident, Axon is there. Once the investigation has been handled, the team will provide a report with details, incident severity, and actionable recommendations, in an easy-to-digest format
"By the end of the second day after the SolarWinds attack had been publicly disclosed, I had done executive updates confirming the status of where we were related to the threat. That was purely based on what we had gotten from Team Axon in the form of in-platform reports after they sweeped IOCs and confirmed that our environment was clean."
— CISO, FinServ Company in the US
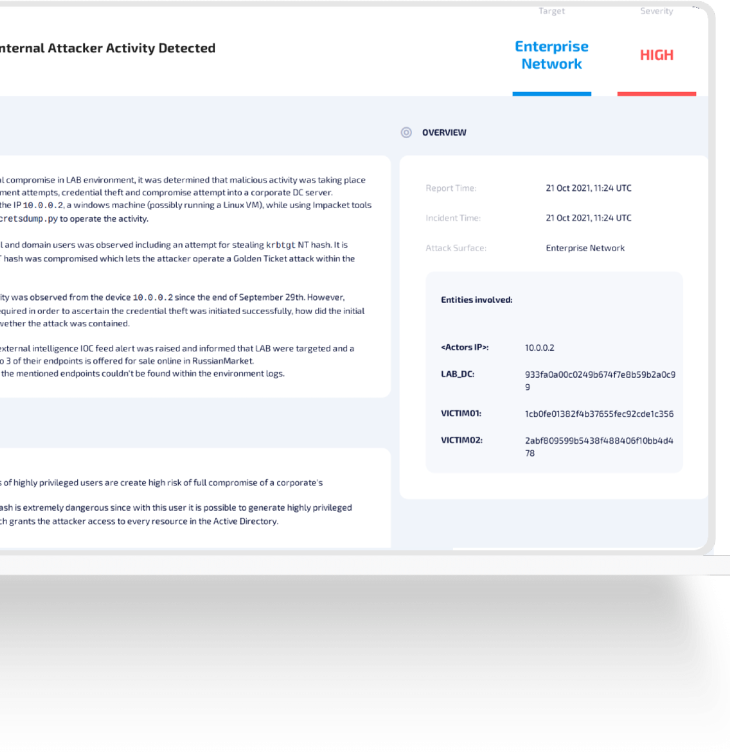
Axon Reports
If Team Axon finds a potential attack in your environment, they’ll send you a human-readable report, containing:
- Threat summary
- Risk assessment
- Recommendations and immediate action items
- Thorough timeline and kill chain analysis
- Relevant data sources for hunting
PROACTIVE THREAT HUNTING
Fill in your blind spots
Today’s security teams are choosing to take a proactive approach to threat prevention. Team Axon performs periodic threat hunting activities over your environment, helping your team detect and respond to emerging threats that may have been missed by traditional security measures.
We go where you don’t
Team Axon analyzes raw logs in the “dark corners” of your network where your team isn’t necessarily looking.
Reports your boss gets
If a threat is found, Axon alerts your team and provides a detailed report with best practices and recommendations.
How’s my hunting?
Periodic security posture and hygiene reports help your team stay above water.
Love for the community
Interesting research findings are often published on X (formerly Twitter) or on the Hunters blog.
“Overall, the support from Hunters was phenomenal. But what was really meaningful early on in our POC was Team Axon. They were the team of professionals that identified the security incident that we had across multiple environments, and told the narrative quickly, accurately, and concisely.”
— John Fung
(Former) Deputy CISO, Cimpress

Keep up with Team Axon
Frequently Asked Questions
Is Team Axon an MSSP?
No, Team Axon is not an MSSP. It is an additional service that can be purchased with Hunters SOC Platform to complement your existing team with added threat hunting expertise.
How often do Rapid Response campaigns take place?
Unfortunately, adversaries don’t follow a schedule, but Team Axon makes sure to constantly monitor the news for public announcements of new threats and vulnerabilities.
What sources do Team Axon monitor to keep informed on emerging threats and TTPs?
There’s no defined list of sources the team monitors, but they do track CISA Alerts, MSFT alerts, and other official sources, and follow threat intelligence communities on Twitter and beyond to get ahead of new threats and vulnerabilities.


