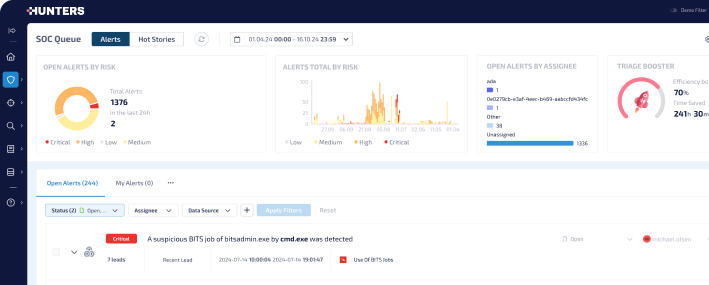
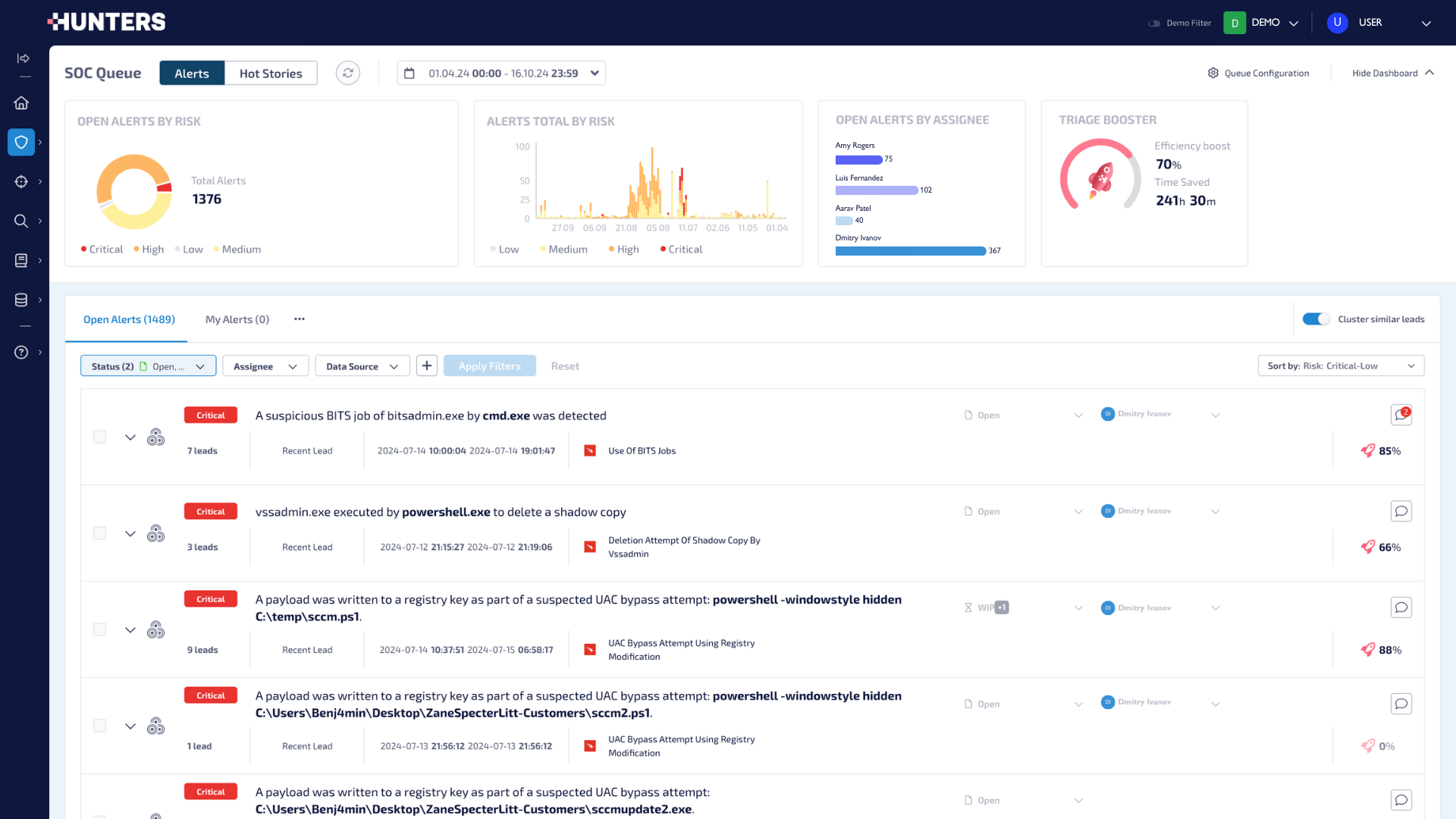
A SIEM that works for you, not the other way around.
Hunters Next-Gen SIEM automates manual tasks using AI and machine learning, to break through the noise
.png)
Works out-of-the-Box
Deploys in days with pre-built integrations and verified detection rules

Only critical threats
Reduces alert triage by 80% and removes false positives
.svg)
Automates investigation and response
Arms your team with full threat context and next steps
SECOPS UPLEVELED
%
False Positive Reduction
%
Reduction in MTTR
X
Triage Efficiency Boost
Streamline Your Security Operations
Hunters Next-Gen SIEM leverages AI and automation to prioritize, investigate, and respond to alerts
.png)
A Force Multiplier For Your Existing Tools
Connect data across your entire stack to your Next-Gen SIEM for full threat context and to identify threats missed in isolation

Azure

Google Cloud Platform

1Password
.png?width=184&height=247&name=21182961%20(1).png)
Beyond Trust

Microsoft Defender for Endpoint
SentinelOne
Don’t Just Take Our Word for It...
Hear what Hunters’ customers are saying about Next-Gen SIEM:
“Hunters allows to quickly increase threat detection coverage across different environments, reducing detection, investigation, and response times while saving on security operations costs.”
John Fung
— Former Deputy CISO at Cimpress
"After deploying Hunters' platform, we could use its functionalities to essentially manage any security alerts events, and accordingly, we can respond to any security incidents in a timely manner. That way, we can also reduce any possible business impacts."
Yeunkwan Kim
— Security Engineering Manager at Unzer
“Hunters is a fantastic partner for us. Hunters handles our detection engineering and all the major things we need to detect and respond to. Hunters takes our data and drops the raw feed into a shared snowflake database where then my my team can build our own data models and applications”
Cyrus Tibbs
— Chief Information Security Officer at Pennymac
Recommended resources
Webinar: Supercharge your security team with Agentic & Co-Pilot AI
GitHub Actions Supply Chain Attack(s): tj-actions & reviewdog
Just Released: SIEM Buyer's Guide for Small SOC Teams in 2025
Ready to see Hunters Next-Gen SIEM in Action?