Thought Leadership, Company Updates
New Game-Changing Capabilities to Enable the Journey Beyond SIEM
- By Sarah Breathnach
- 6 minutes to read
If you’ve been following Hunters for a while now, you may have noticed that we’re fully committed to supporting our customers’ transition to a security operations center beyond the legacy SIEM. In order to do so, Hunters’ XDR platform acts as a SOC decision support system, aligning existing security tools into a cohesive incident detection, investigation, and response platform that applies autonomous attack analytics to identify real incidents with context to drive rapid, effective response.
Our team is firmly committed to developing the platform that will become the main, central tool for the SOC - many of our customers are realizing value from this already! - and so constantly developing new capabilities and upgrades to existing ones is key to stay at the forefront of security operations tools.
Read on to learn more about our Enhanced Auto-Investigations, Custom Detections, and Dashboards & Reporting.
Enhanced Automatic Investigations
One of the critical gaps in threat detection and response is precisely what comes in between those two, which is the “understanding phase”. This phase contains the investigation activities that need to happen for the Analyst to be able to understand what was detected, what assets were affected, what telemetry is correlated to a specific alert, and what are the next steps that will define the response.
But that process of manually stitching together siloed threat signals is extremely time-consuming, often frustrating, and in several cases inaccurate too, due to the lack of context to alerts and visibility over all the connected threat signals.
Hunters’ automatic investigations eliminate hundreds or thousands of daily alerts, giving security analysts more time to work strategically - and these just got a major upgrade.
Auto-Investigations are about providing more context to the alert to enable a more thorough and effective understanding and triage. This is achieved by enriching the alert with additional supporting data, correlating information with external sources, and applying out-of-the-box knowledge to facilitate faster and more accurate decision making, ultimately expediting valuable response time. In order to do so, investigations now focus on the key entities involved in an alert and all of its relevant associated attributes, which allow to derive an explanation on what happened and relevant insights.
Auto-Investigations are grouped into key meaningful entities that are related to the alert: host, person, process, etc. each with its own related attributes, enrichments and activity data that enable deeper understanding of the inter-relation between them and as a result, of the maliciousness of the alert.
An example of an Auto-Investigation for an “AWS Console Login from Host without an EDR Agent” alert
Custom Detections (or “Rule-Writing” 2.0)
Hunters’ pre-built Detections provide comprehensive coverage out-of-the-box, but customers can also add their own detection logic into the platform to easily query the data without writing a single line of SQL.
While we’re firm believers that the rule-writing approach for detection that legacy SIEMs employ is cumbersome, noisy and inefficient, no one knows better the security ecosystem of the organization than their SOC team does, and so having the ability to customize detections that fit their very own environment on top of all the out-of-the-box Hunters’ TTP-based detections is key.
With Custom Detections users are able to add their own detection logic on top of the ingested and normalized data, defining their own detection rules or using logic taken from external public repositories in order for the platform to apply that logic on the ingested data. As part of the Custom Detections feature, users can also define the base score, associated MITRE TTPs, and other metadata. Users are also able to enjoy additional scoring layers that the platform will automatically apply on top of the customers’ detections to help prioritize the real threats and remove the noise.
Creation of a Custom Detection in the Hunters’ portal to detect rundll32.exe processes
So how does the Analyst consume all of this information in a smart and actionable way?
Hunters’ Security Operations screen includes all interfaces geared towards the tier 1 and tier 2 analyst teams within the SOC, and it displays prioritized alerts which have passed a customizable, predefined score threshold. It’s important to note that the prioritized alerts can be: either those generated by existing security tools, the Custom ones that users can easily write in the portal, and those generated by Hunters’ own detections that come out-of-the-box. This is very important to note, as unlike other XDRs in the market that simply ingest data and do a quick alert triage, Hunters XDR adds an analytic layer powered by hunting capabilities encoded into the system that looks for weak signals that other tools can miss.
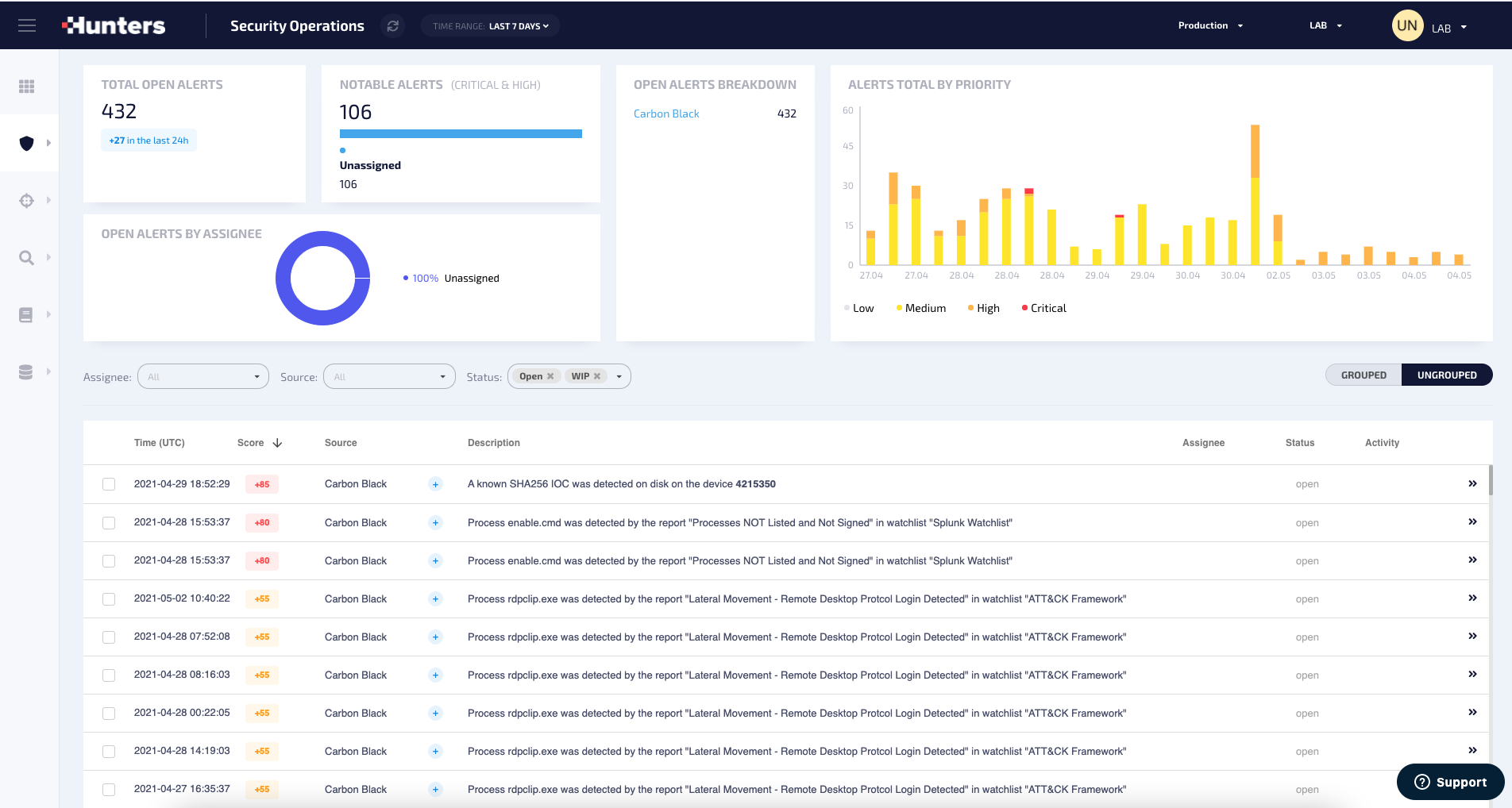
Hunters' Security Operations Screen
Dashboards & Reporting
Hunters’ Dashboard and Reporting capabilities allow security teams to use Hunters’ data (alerts, leads, MITRE TTPs, etc.) as well as raw data from the security data lake to create custom dashboards to visualize SOC metrics, monitor activity in the network, analyze threat trends and track the organization's security posture.
Dashboards allow users to generate and share reports with peers as well as different teams and functions of the organization.
These are some of the key use cases of this new feature:
- Monitor Security Team operations
- Track security threat trends
- CISO Dashboard
- Executive IT-Security report
- Organization security posture tracking
- IT-Security visibility
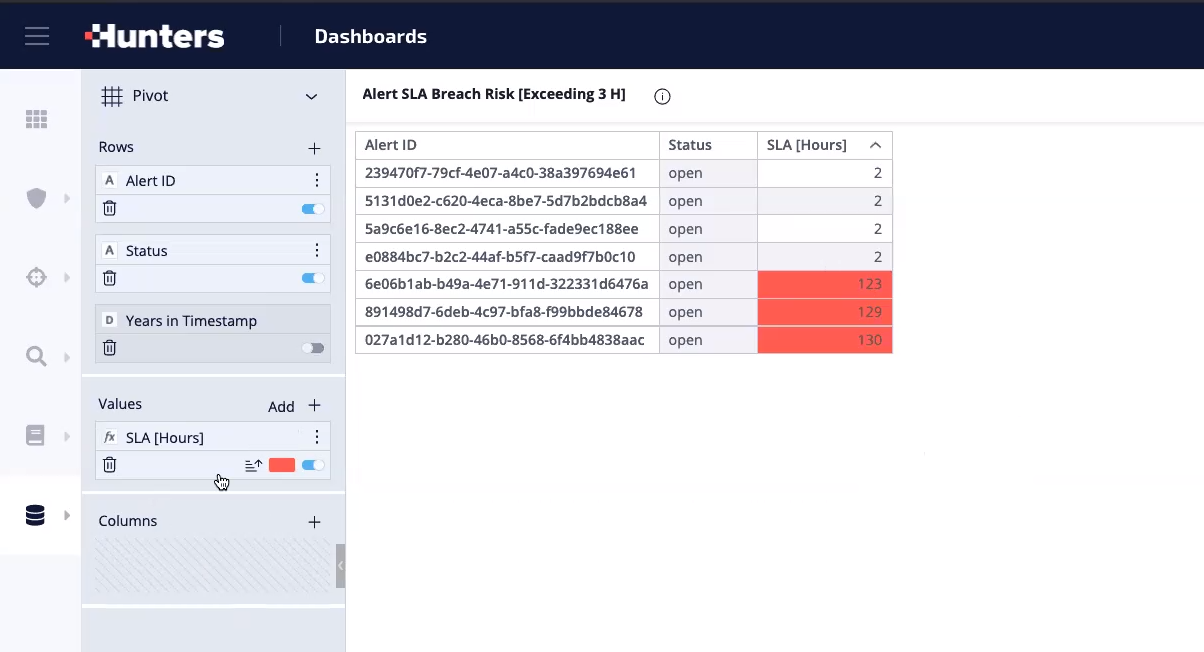 An example of a Custom Widget for Alerts SLA
An example of a Custom Widget for Alerts SLA
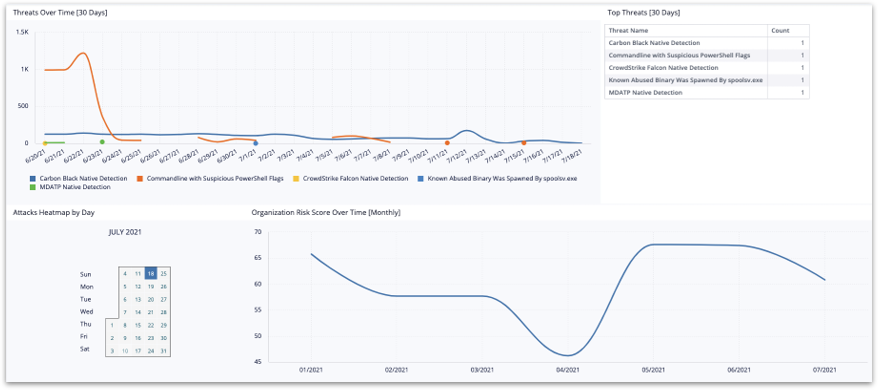
An example of a CISO Custom Dashboard
Want to learn more on how Hunters XDR can support you in your Journey Beyond the SIEM?
Request a demo with our experts today!


