Reducing investigation time by up to 85% with Hunters’ Rapid Automatic Investigation
- By Yuval Zacharia
- 4 minutes to read
We have just released a series of enhancements to the Automatic Investigation in the Hunters SOC Platform to drastically reduce the time to triage and investigate alerts.
In near real-time, security analysts can view the entities and targets involved in an attack, such as specific individuals, servers, or executables, getting a clear picture of the Who, What, Where of an attack. Furthermore, this critical information can be used to expedite the remediation and containment process when integrated with SOAR tools via the Hunters API.
Why Automatic Investigations are so important to us
Hundreds of alerts are triaged and investigated each day by security teams with the goal of understanding the threats, their scope, and their potential impact. An analyst first needs to have a good understanding of the threat and attack surface and know what questions to ask to refute or convict the suspicious activity and identify the impact on the organization to mitigate the threat holistically.
Furthermore, security analysts need to have a good understanding of the data and its structure, verify they have all the necessary permissions to access the data, and be able to query the data in order to leverage it for the investigation.
At Hunters, we seek to empower security teams with the necessary knowledge to conduct attack scoping, investigate, and mitigate attacks, while reducing inefficient operations and increasing team velocity without adding more staff to handle higher volumes of alerts.
The Automatic Investigation in Hunters SOC Platform aims to replace manual and repetitive actions that run down analysts while providing extensive security context through cross-correlation and enrichment of the data. Analysts can look at a complete incident picture that’s easy to understand, triage, and act upon at a dramatically accelerated pace.
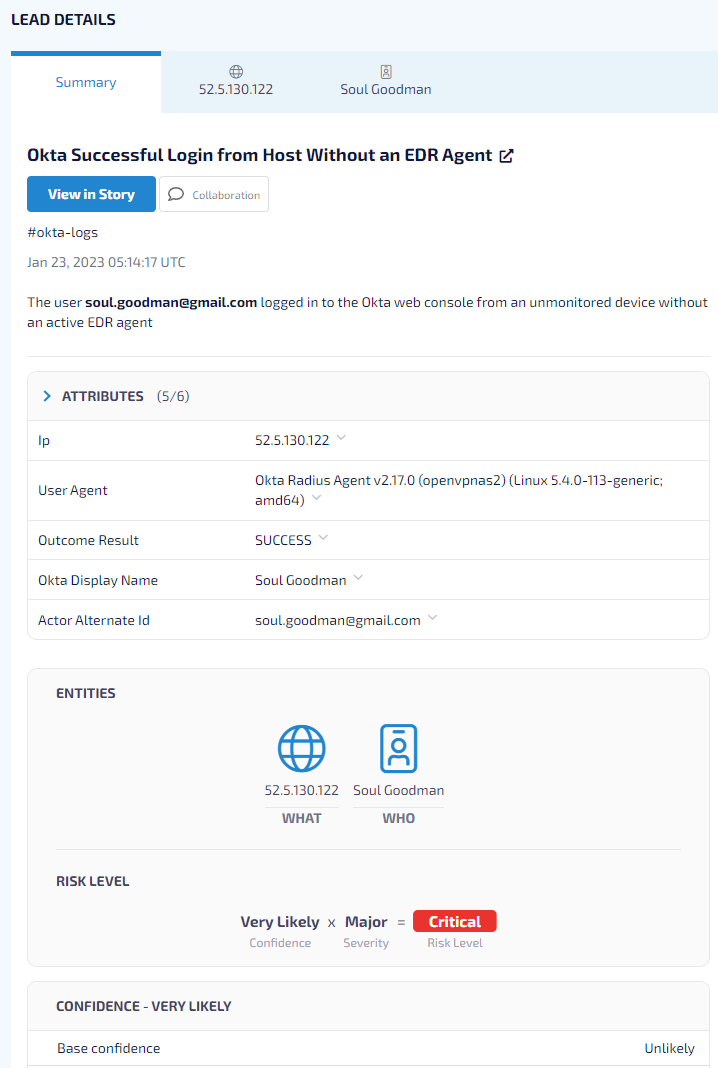 A sample Auto-Investigation summary on the Hunters SOC Platform showing the key entities of an alert generated after a user logged in to the Okta web console from an unmonitored device without an active EDR agent, as well as the Risk Score associated with it
A sample Auto-Investigation summary on the Hunters SOC Platform showing the key entities of an alert generated after a user logged in to the Okta web console from an unmonitored device without an active EDR agent, as well as the Risk Score associated with it
How does it work?
The Automatic Investigation process relies on the availability of data from multiple data sources. This presents a challenge, since some data might not be available when the alert is generated. Furthermore, some of the advanced Automatic Investigation logic provided out-of-the-box looks for information that explicitly happens after the original event.
For instance, when a potentially malicious process is detected, Hunters collects data on the actions taken by the process after its initial execution. Looking for clues such as dropped suspicious files or network connections that may suggest the presence of a backdoor or exfiltration activity.
To speed up the investigation process, we have split the Automatic Investigation process into two phases:
- Rapid Automatic Investigation - This initial investigation for rapid attack scoping takes only a few minutes to complete and provides analysts with a basic framework and details of the possible threat.
- Advanced Automatic Investigation - On top of the initial basic layer of information, Hunters provides a deep analysis of the threat evolution inside the organization that does not exist at the time of detection, such as the execution tree of a suspicious process, network connections, or compromised user behavior. This layer takes up to an hour to complete as it requires following up on the progression of the threat, and connecting both layers of information together to provide the full picture.
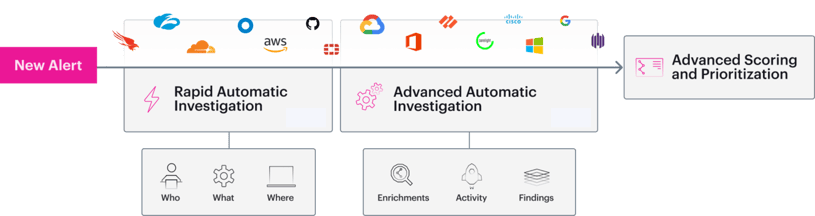
Hunters Automatic Investigation Pipeline
By separating the process to phases, the system is able to provide first data points about the possible threat within minutes, allowing analysts to perform an initial inquiry into the threat while the system continues to enrich this entity with data from across the attack surface to provide greater context and understanding.
With the newly released Rapid Automatic Investigation step in the full investigation process, we will further support smart prioritization of alerts and incidents, and continue reducing the redundant manual work in the triage and investigation phases.
If you want to learn more about Hunters SOC Platform and how it can help your security team, schedule a demo with us or take a product tour.


