Hunters AI-Assisted Investigation: Powering Confident Decision-Making for SOC Teams
- By Yuval Zacharia
- 7 minutes to read
At HuntersCON, we introduced a new way for Security Operations Center (SOC) teams to boost clarity, speed, and confidence with Hunters AI. Now in Open Beta, Hunters AI-assisted investigation is designed to give analysts tailored context, explanations of findings, and suggested next steps for an investigation.
Key capabilities to empower your SOC
In today’s landscape, visibility is key. SOC teams face a daunting volume of data generated by their organization, including data from the security tools in their tech stack. When it’s time to investigate malicious activity, analysts need to review—and make sense of—all that data to understand what is happening and take appropriate action. With a lean team, limited time and available resources can make this extra difficult.
Enter Hunters AI. Hunters AI is an advanced, continuous security intelligence layer that finds attack patterns and autonomously detects, analyzes, and supports analysts in their action against cyber threats, empowering security teams with unparalleled speed and precision. Honing in on what AI is really good at today - summarizing and transforming data for the end user - Hunters AI transforms raw alert data into insights that help analysts act decisively:
- Contextual Summaries: Each alert includes a distilled summary that anticipates questions a seasoned analyst would ask, surfacing the most relevant information. Whether it’s the significance of a specific IP or the potential impact on your environment, this summary injects useful context directly into scoring.
- Relevant Explanations: Hunters AI takes findings a step further, explaining each one with context—whether it's an unusual access attempt, IP analysis, or activity relevant to a user’s role. This layer of explanation bridges the gap between junior and senior analysts, equipping all team members with the background needed for effective decision-making.
- Suggested Next Steps: After breaking down the findings, Hunters AI suggests the next steps to move the investigation forward and guides the analyst to specific areas within the platform to do so (e.g., IOC search, process tree, etc.). These steps are built from insights Hunters AI has gathered about the threat’s context, giving analysts a direct path to act confidently and effectively.
Real-world impact: assisting the investigation workflow
The Hunters Next-Gen SIEM seamlessly integrates AI functionalities into the investigation process. Each alert in the SOC Queue is presented as a Lead, a potential security incident or threat identified through security monitoring activities or other sources of security intelligence. Once an analyst opens the details, they can see a centralized view of all related information to that particular alert and trigger Hunters AI with a simple click of a button.
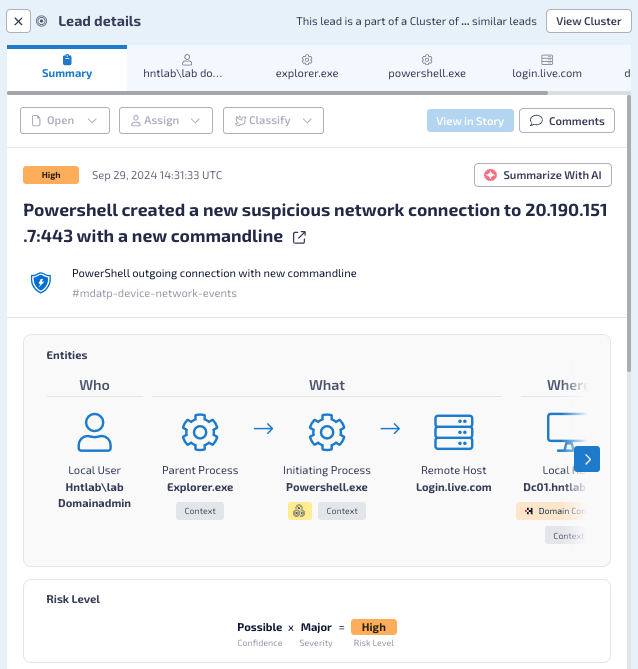
First, Summarize Lead. Summarize Lead will generate key outputs (based on investigation details) designed to ensure the analyst has a clear understanding of what is happening (e.g., providing the “what am I seeing,” “why should I care,” “why am I seeing it” and “who is involved” context) - the more context associated with the alert, the more robust the output. This is especially critical when an alert is associated with multiple similar alerts.
-1.png?width=502&height=367&name=unnamed%20(1)-1.png)
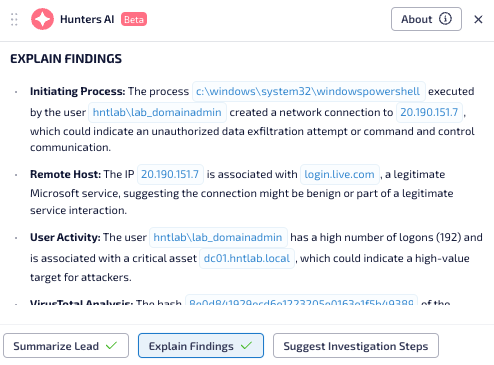
Next, Explain Findings will deep-dive into findings from the Hunters investigation pipeline, scan the results, and provide the rationale as well as a high-level thesis on the meaning of the results—up-leveling what is most important and impactful for the analyst to know.
Lastly, Suggest Investigation Steps takes the information from Summarize Lead and Explain Findings to suggest the next steps and provide guidance on relevant features within the Hunters Platform for the analyst to continue their investigation. This guidance provides analysts of all experience levels with the clarity they need to make proactive, decisive moves on every alert.
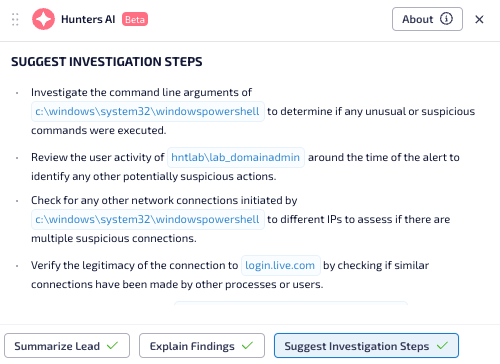
This workflow summarizes information, eliminates toggling, and empowers SOC teams to respond faster and more effectively. Worth noting, the organizations data remains in a closed environment and is NOT used to train AI models - so you can be assured of privacy.
"[The "Summarize with AI" feature] really helps us a lot, especially since we are a small team, and it saves us time and effort."
- Security Practitioner, Retail Industry
Another step in Hunters' AI strategy
Hunters AI-assisted investigation is another step within our AI strategy. Hunters has been leveraging machine learning capabilities for years - developing proprietary statistical models which power our User and Entity Behavior Analytics (UEBA) detections. By continuously learning the statistical characteristics of user and organizational behaviors, Hunters AI detects subtle anomalies that may signal potential threats. As a result, SOC teams benefit from:
- Reduced Alert Noise: By analyzing patterns at both organizational and user levels, Hunters AI filters out noise, reduces alert volume (by 90%*), and flags high-suspicion events with precision.
- Automatic Detection & Learning: Hunters AI continually adapts to emerging behavior patterns, alerting SOC teams when it identifies suspicious activity and ensuring the detection layer evolves with new threat data.
- Improved Mean Time to Detect (MTTD): By automating anomalous behavior detection, Hunters AI equips SOC teams with relevant data to investigate high-priority incidents faster.
Looking ahead: a glimpse into Hunters' AI vision
Hunters AI-assisted investigation is yet another step in executing a broader AI vision: to empower SOC teams with AI that intuitively understands their workflows, anticipates next steps, and autonomously drives complex security tasks to completion. Our goal is to guide analysts seamlessly toward proactive and decisive action, aligning with Hunters' commitment to democratize cybersecurity expertise through technology and automation.
Curious to try out Hunters AI?
Current customers, if you’re interested, connect with your Hunters representative to join the Open Beta.
For those new to Hunters, this is just the beginning. Stay tuned for January, when we’ll share more about our AI vision and strategy, enabling SOC teams to dive deeper and respond faster than ever before.
*based on internal analysis


