Automation has untapped potential in security operations
- Oct 18, 2022
- By Patrick Vandenberg
- 5 minutes to read
Security operations teams are continually searching for more technically advanced and cost-efficient ways to defend the enterprise. Today, a key topic in this discussion is automation. But while automation in security has been around for years, it is still a vastly underutilized opportunity.
Automation is still on its first steps in security
In security operations, the conversation around automation is heavily centered on security orchestration, automation and response, or SOAR. But automation still has limited application across the full SOC workflow. It’s true that response automation is well adopted and effective, but it’s also the last phase of the security operations workflow. Focusing automation exclusively on SOAR means ignoring several key phases - data ingestion and management, detection, and investigation and triage - which all have to happen before response automation can begin. Clearly, automation has untapped potential in security operations. So what’s holding it back?
There are two misconceptions around automation and security that are holding back exploration and adoption.
-
- Automation is not only SOAR
Currently, SOAR appears to hold reins on ‘automation’ in security contexts. In recent CISO round tables, when we raised the topic of automation, we found that discussions instinctively focused on mitigation actions and orchestration with IT operations, despite attempts to broaden the automation discussion. There appears to be a general knowledge gap about the key phases in security operations that can greatly benefit from increased automation.
- The Fully Autonomous Myth
The other misconception is that automation in security means full automation. There’s a common, but mistaken, idea that automation can or will “take over” a function completely, which naturally inspires some resistance. But in practice, this is not where the opportunities and benefits lie. Security operations teams face critical challenges in handling the volume and variety of data, the heavy overhead in detection engineering and maintenance, and the manual, repetitive, and prolonged investigations. All of these challenges can benefit from automation, while leaving plenty of responsibility for security practitioners to apply their expertise. “Fully autonomous” is not necessary to realize significant benefit, nor is it the best solution - the skills of security engineering and security analysts are always critical and in play to help secure their business.
- Automation is not only SOAR
The Automation Opportunity
Now that we have addressed inhibiting misconceptions about automation in security, let’s explore the vast opportunity available to the security workflow.
- Embrace the Data
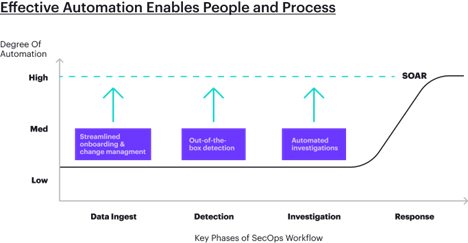
The combination of both volume and variety of data from the expanding attack surface create a downstream challenge for SOC workflows. It's one thing to simply connect and ingest data, but working with the cloud-scale data volumes of today, from a wider variety of sources, imposes new challenges and limitations that security teams must grapple with.
Security data lakes combined with data engineering offer a solution to this problem by automatically normalizing the data ingested into the platform. Applying a unified schema to normalize data from all sources into a common frame of reference, security data lakes enable analysts to jump straight into investigations, without needing to deeply understand different log formats. This data architecture also tends to be more cost effective, allowing security teams to no longer compromise by turning off noisy firewall or application firewall logs. We are constantly preaching visibility in security, yet the limitations of traditional SIEM deployments force many teams to compromise on that visibility–this doesn’t make sense from a security perspective.
- Build in the Detection
A massive burden on security engineering today is the need to create and maintain an endless expanse of rules to detect malicious activity, even though the vast majority of attack activity, and the related threat data, is common across almost all organizations. So why do so many organizations staff teams of detection engineers to find the same thing? The vast majority of threats follow the 80/20 rule: if all organizations are seeing approximately 80% of the same data, there is a tremendous economies of scale opportunity.
Introducing automation from pre-packaged detectors, ready to operate out-of-the-box, can offload this 80% of detection workload, providing the opportunity for security engineering staff to focus on the detections most specific to their organization or industry.
- Automate the Investigation
Security operations is notorious for its high analyst turnover. One contributor to this challenge is the repetitive, mundane and manual investigation work that requires constant switching across numerous tools, as well as weeding through a high degree of false positives. This routine not only exhausts analysts leading to burn out, but it also impedes upskilling by reducing the time available to spend on more challenging investigations. Interestingly, in recent boardroom discussions we encountered that investigation was the phase of security operations least associated with automation (response being the predominant phase).
When data is fully ingested, normalized, and retained for accessibility, detection is now able to be effectively automated, and at considerable scale. This automation then empowers automated investigations, with features like full search on retained data, correlated graphs, automated enrichment, and attack stories that link and present the who, what, and where of an attack on an easy-to-consume timeline. These outcomes of automated investigation enable security analysts to digest, inspect, and quickly triage risk-prioritized attacks, instead of the limited and prolonged manual investigations still required by SIEMs.
When a system is architected for today’s IT environment, applying automation empowers further efficiency in the SOC workflow. Hunters SOC Platform focuses on that dynamic, designed to manage the scale and variety of data, using automation to align and streamline the security operations workflow. Hunters tackles data, detection, investigation and response in a single integrated, low-maintenance platform that fully exploits the advantages of a cloud-based SaaS solution.



