SUNBURST: How to Minimize the Risk of Future Nation-State Attacks
- By Hunters Research Team
- 7 minutes to read
Last week we witnessed what many are calling one of the biggest cyber attacks in recent times. SUNBURST, the malware installed on SolarWinds’ Orion product line in what seems like a nation-state sponsored supply chain attack, has made its way to the headlines worldwide, and for good reason.
Throughout this brief post, we will present some of the key Tactics and Techniques used by the nation-state actors in the malicious campaign, using the MITRE ATT&CK framework as a baseline, and will provide recommendations on how organizations can minimize the risk of exposure to complex attacks and the damage inflicted by them.
Background
SUNBURST, when installed, can allow an attacker to compromise the server in which the Orion products run. Namely, the nation-state attacker, crafted a very sophisticated backdoor which was disguised as a legitimate software update from SolarWinds’ Orion products, as was disclosed by FireEye on December 13th. Unbeknownst to them, dozens of thousands of public, private and government organizations, including tech giants and government agencies such as the US Treasury and Homeland Security departments, have installed the malware in their systems in the past few months, and the malware could have been in stealth since as early as March of this year.
For Security Operations teams, this type of malware is nothing less than a nightmare. Firstly, there is the urgency of understanding whether the malware is present in any part of the organizations’ network. Should that be the case – which is the reality of at least 18,000 companies so far – the incident response team and threat hunters need to thoroughly understand whether the backdoor has actually been used to extract information, and what traces (if any) has it left in the network. Allegedly, post compromise activity following this supply chain compromise has included C2 Communication, Lateral Movement, Defense Evasion and Data Theft.
SUNBURST High Level Attack Flow Analysis
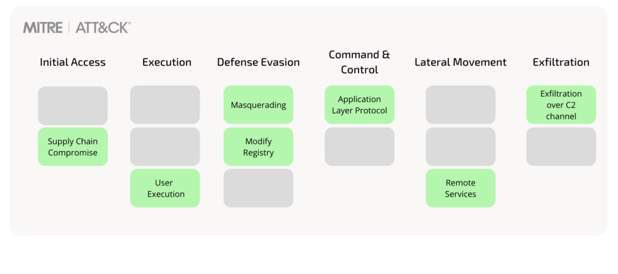
Initial Access
The Initial Access for the malware is conducted by a Supply Chain Compromise, via a malicious DLL file that the actor successfully installs in a SolarWinds update package.
Execution
When the package is executed, the DLL is executed and the machine gets infected. The main capabilities of the malware include: Awareness activity and Execution capabilities, as well as Scripting capabilities like PowerShell.
Defense Evasion
The malware enumerates the host for the existence of specific drivers, services and processes. These are mostly security controls used by organizations, or tools used by security researchers. If any entries in the list are found, the malware will terminate and will halt any further execution. Additionally, the malware attempts to disable specific security controls detected on the host by modifying registry key settings.
Command and Control
After a dormant period of up to two weeks, the malware communicates to a Command and Control server, using a SolarWinds legitimate Application Layer Protocol, which also serves for Defense Evasion. Other Defense Evasion techniques used by the actor are impersonating legitimate entities from the network, as well as evading known endpoint security components.
Lateral Movement
The actor later uses various techniques, such as creating new tasks on remote machines using PowerShell, for lateral movement to points of interest.
Exfiltration
The attack ends in Exfiltration of relevant data, such as emails via PowerShell email commands, or password-protected archives containing sensitive data from the victim’s servers, via standard HTTP requests.
SolarWinds Attack – What To Do Right Away
It is recommended to perform a comprehensive IOC sweep (using the IOCs previously published by FireEye as a follow up to the initial write-up) across all hosts in the network, as well as examine for any abnormal Federation trusts in your Azure tenants or any signs of administrative actions from unmonitored endpoints (e.g., IP addresses from which no EDR agent has reported).
How to Prepare in the Long Term
The SolarWinds breach is not over: identifying all the potential points of exposure and completely blocking them can be quite cumbersome, especially in big IT environments. In order to keep track of your organization’s exposure to the SolarWinds breach, we recommend several security posture enhancements that will increase the likelihood of detecting the SUNBURST backdoor and its subsequent activities, as well as other complex threats in the future:
- Security Data Lake. This incident has shown the significance of retaining security log data for a long period of time. The SolarWinds incident started as early as March 2020, about 9 months before it was initially discovered. Maintaining a security data lake which stores security, network and relevant application logs with adequate retention will prove vital in the ability to uncover and investigate such events.
- Visibility. Ingesting security logs is not enough: it is important to ensure that your current security controls (e.g., EDR) are deployed on all hosts in the network to ensure proper coverage. Proper visibility will not only allow for swift detection, but also assist in discerning what actions took place on the host, what traffic traversed your network devices, and what applications users accessed and from where. We therefore recommend to ensure that all relevant controls are deployed hermetically and that all relevant IT and security infrastructure is forwarding logs as expected.
- Asset Management. Having an organized and updated inventory of relevant assets, both hardware and software (programs, virtual machines, software versions etc.) is of extreme importance in order to quickly determine whether a specific breach is relevant to your organization. Visibility dashboards that summarize such information, and get automatically updated and alert on unexpected changes, are a real asset for any security team.
- Proactive Threat Hunting. We believe in a proactive approach for anomaly detection. Conducting proactive threat hunting over security logs, using efficient data analysis tools and anomaly detection techniques, should be an essential part of any security strategy. It is also beneficial to have tools to automate the hunting process, in order to invest your time on hunting and not on tedious supplementary or repetitive tasks. For example, having an automated IOC sweep mechanism can save a lot of time, instead of manually querying the data each and every time.
- Connecting Security Telemetry. The hybrid IT environments within organizations and the disperse solutions lead to siloed detection as well. Without interconnecting data sources, single-sensor security solutions are most likely going to miss advanced threats, especially those that move laterally in the corporate network. Interconnecting and correlating security telemetry with Extended Detection and Response (XDR) solutions can help the organization eliminate blind spots and detect faster across the entire stack with accurate findings.